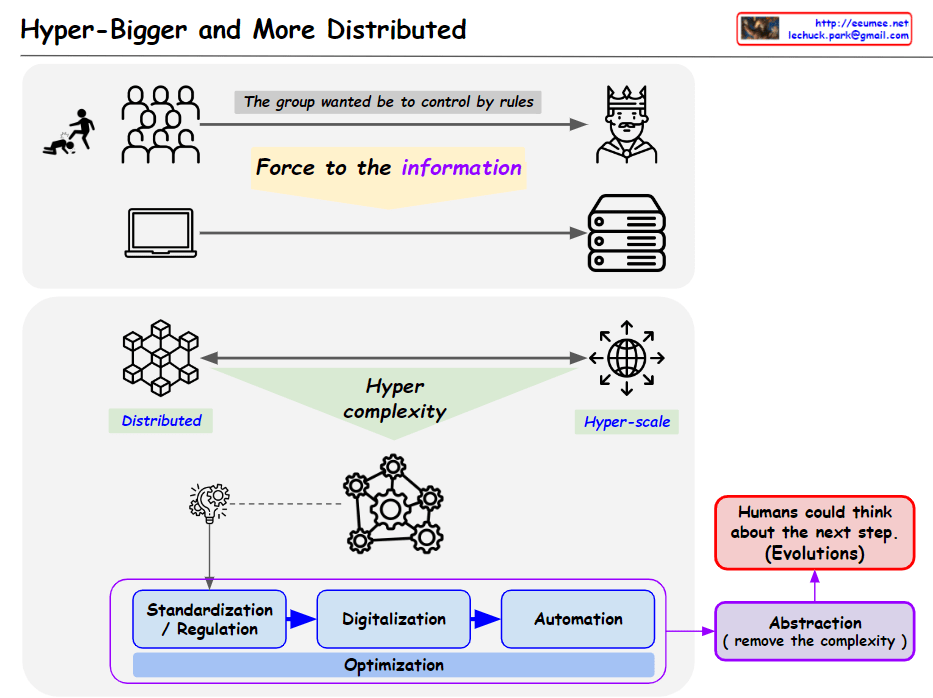
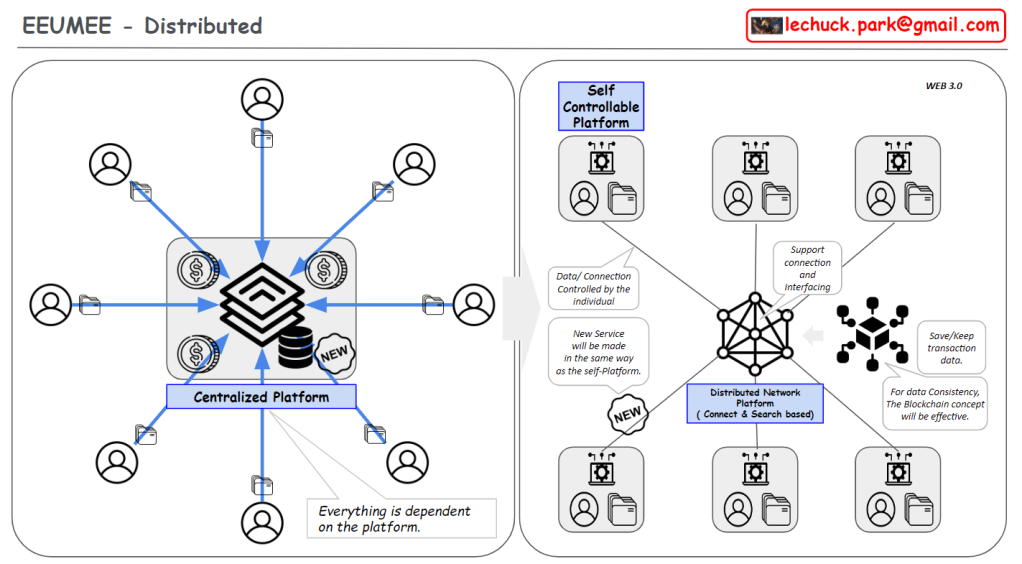
The evolution of AI data centers has progressed through the following stages:
- Legacy – The initial form of data centers, providing basic computing infrastructure.
- Hyperscale – Evolved into a centralized (Centric) structure with these characteristics:
- Led by Big Tech companies (Google, Amazon, Microsoft, etc.)
- Focused on AI model training (Learning) with massive computing power
- Concentration of data and processing capabilities in central locations
- Distributed – The current evolutionary direction with these features:
- Expansion of Edge/On-device computing
- Shift from AI training to inference-focused operations
- Moving from Big Tech centralization to enterprise and national data sovereignty
- Enabling personalization for customized user services
This evolution represents a democratization of AI technology, emphasizing data sovereignty, privacy protection, and the delivery of optimized services tailored to individual users.
AI data centers have evolved from legacy systems to hyperscale centralized structures dominated by Big Tech companies focused on AI training. The current shift toward distributed architecture emphasizes edge/on-device computing, inference capabilities, data sovereignty for enterprises and nations, and enhanced personalization for end users.
with Claude