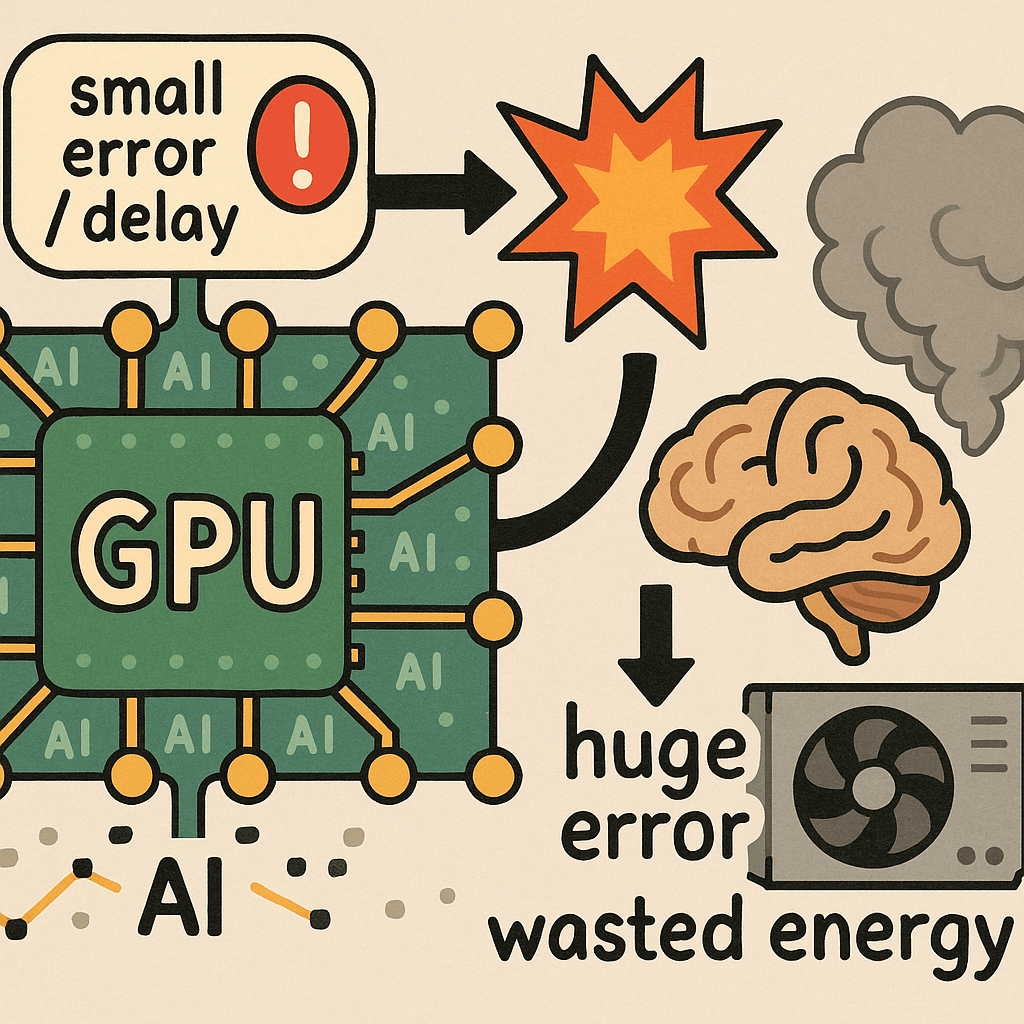
This image illustrates a comparison between two approaches for Prediction with Data.
Left Side: Traditional Approach (Setup First Configuration)
The traditional method consists of:
- Condition: 3D environment and object locations
- Rules: Complex physics laws
- Input: 1+ cases
- Output: 1+ prediction results
This approach relies on pre-established rules and physical laws to make predictions.
Right Side: Modern AI/Machine Learning Approach
The modern method follows these steps:
- Huge Data: Massive datasets represented in binary code
- Machine Learning: Pattern learning from data
- AI Model: Trained artificial intelligence model
- Real-Time High Resolution Data: High-quality data streaming in real-time
- Prediction Anomaly: Final predictions and anomaly detection
Key Differences
The most significant difference is highlighted by the question “Believe first ??” at the bottom. This represents a fundamental philosophical difference: the traditional approach starts by “believing” in predefined rules, while the AI approach learns patterns from data to make predictions.
Additionally, the AI approach features “Longtime Learning Verification,” indicating continuous model improvement through ongoing learning and validation processes.
The diagram effectively contrasts rule-based prediction systems with data-driven machine learning approaches, showing the evolution from deterministic, physics-based models to adaptive, learning-based AI systems.
With Claude