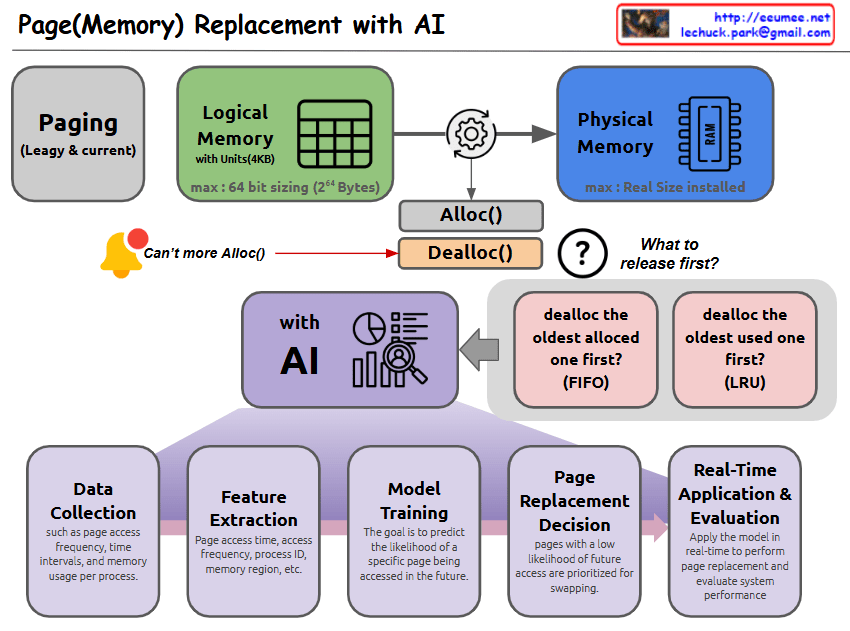
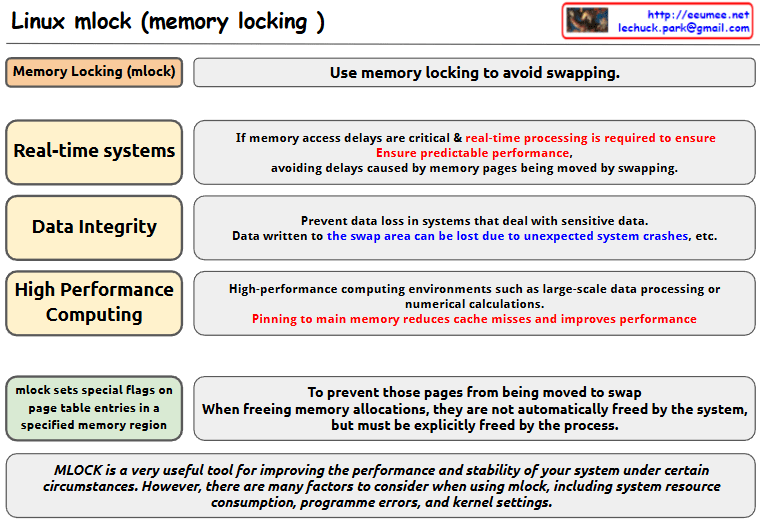
This diagram illustrates the Memory Bound phenomenon in computer systems.
What is Memory Bound?
Memory bound refers to a situation where the overall processing speed of a computer is limited not by the computational power of the CPU, but by the rate at which data can be read from memory.
Main Causes:
- Large-scale Data Processing: Vast data volumes cause delays when loading data from storage devices (SSD/HDD) to DRAM
- Matrix Operations: Large matrices create delays in fetching data between cache, DRAM, and HBM (High Bandwidth Memory)
- Data Copying/Moving: Data transfer waiting times on the memory bus even within DRAM
- Cache Misses: When required data isn’t found in L1-L3 caches, causing slow main memory access to DRAM
Result
The Processing Elements (PEs) on the right have high computational capabilities, but the overall system performance is constrained by the slower speed of data retrieval from memory.
Summary:
Memory bound occurs when system performance is limited by memory access speed rather than computational power. This bottleneck commonly arises from large data transfers, cache misses, and memory bandwidth constraints. It represents a critical challenge in modern computing, particularly affecting GPU computing and AI/ML workloads where processing units often wait for data rather than performing calculations.
With Claude