From claude with some prompting
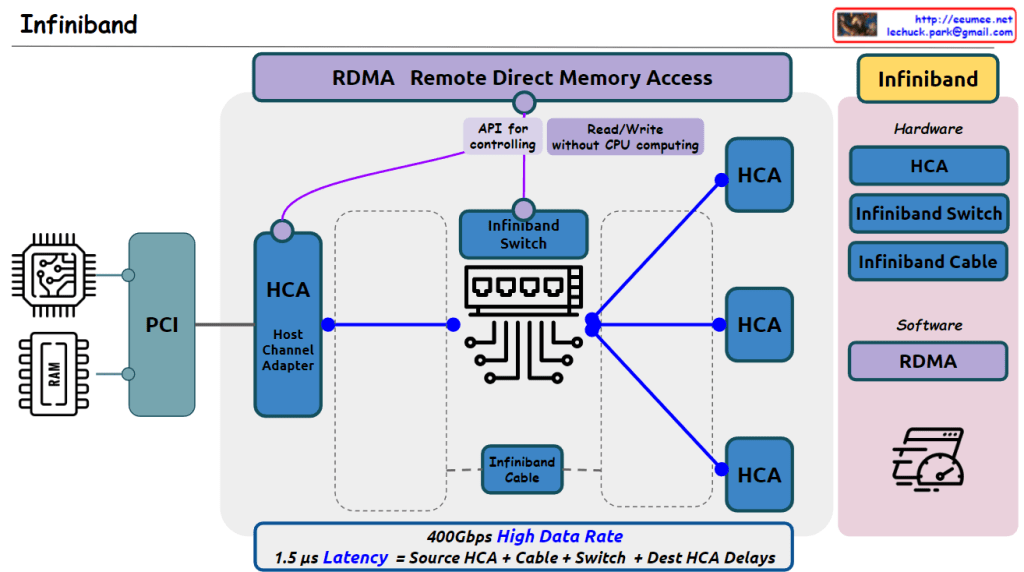
The image correctly depicts the essential hardware elements of an InfiniBand network, including the PCI interface, Host Channel Adapters (HCAs), InfiniBand Switch, and InfiniBand cables connecting the HCAs to the switch.
It highlights RDMA (Remote Direct Memory Access) as a key technology that enables read/write operations without CPU involvement, facilitated by APIs for controlling the HCAs.
The hardware components listed (HCA, InfiniBand Switch, InfiniBand Cable) are accurate.
However, there is one potential inaccuracy in the details provided. The stated latency of 1.5μs seems quite low for an end-to-end InfiniBand communication. Typical InfiniBand latencies are in the range of a few microseconds, depending on the specific InfiniBand generation and configuration.
Additionally, while the image mentions a “400Gbps High Data Rate,” it’s important to note that this is an aggregate bandwidth across multiple links or ports, not necessarily the speed of a single link.
Overall, the image effectively conveys the main concepts and components of InfiniBand technology, with just a minor potential discrepancy in the stated latency value.