From Claude with some prompting
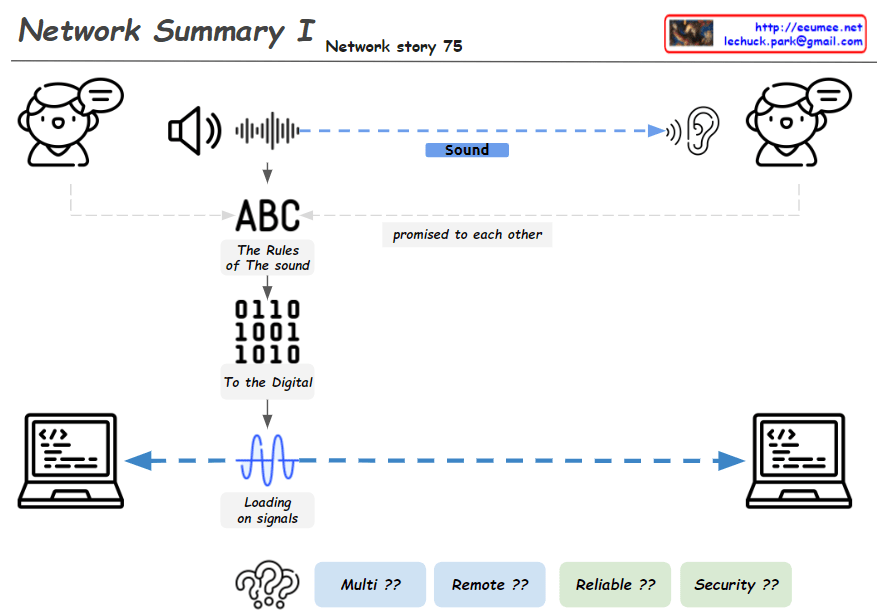
This image, titled “Network Summary I”, illustrates the basic process of network communication in several steps:
- Sound Transmission: It shows sound being transmitted between two people.
- Communication Rules: The phrase “ABC – The Rules of The sound” indicates that there are agreed-upon rules for sound transmission.
- Digital Conversion: It demonstrates how sound is converted into digital signals, represented as “0110 1001 1010”.
- Signal Transmission: The phrase “Loading on signals” along with a waveform shows how signals are transmitted between two computers.
- Network Challenges: At the bottom, the questions “Multi ??”, “Remote ??”, “Reliable ??”, and “Security ??” present key issues to be addressed after establishing a network connection.
This diagram provides a basic overview of how voice communication is converted to digital data and transmitted over computer networks. It then poses questions about how to handle multiplexity, remote connections, reliability, and security in actual network implementations.
By presenting these challenges, the image implies the necessity for more complex networking protocols like TCP/IP and various networking equipment. It effectively summarizes the journey from basic principles of network communication to the complex issues faced in real-world network implementation, serving as an educational tool to introduce networking concepts.