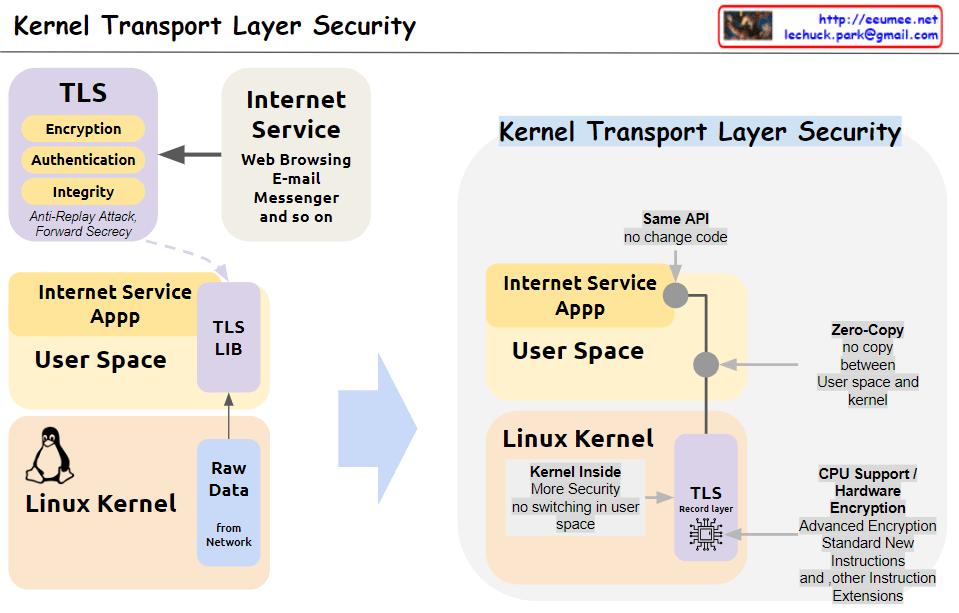
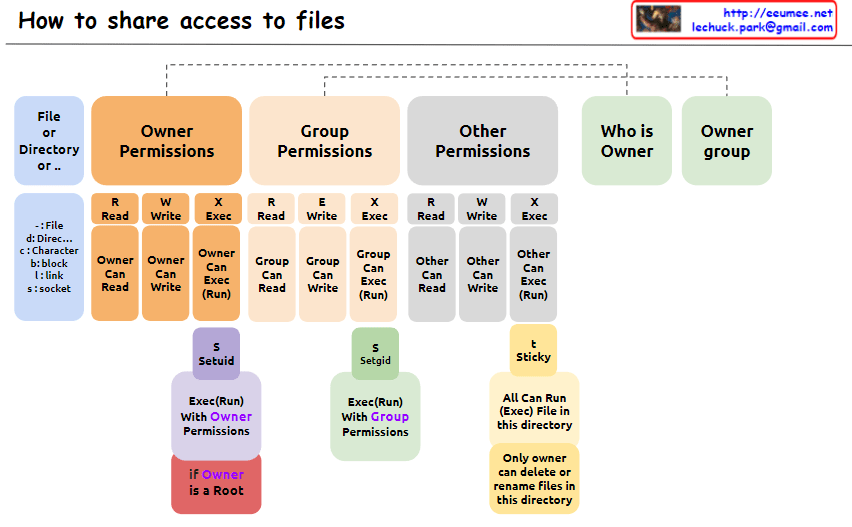
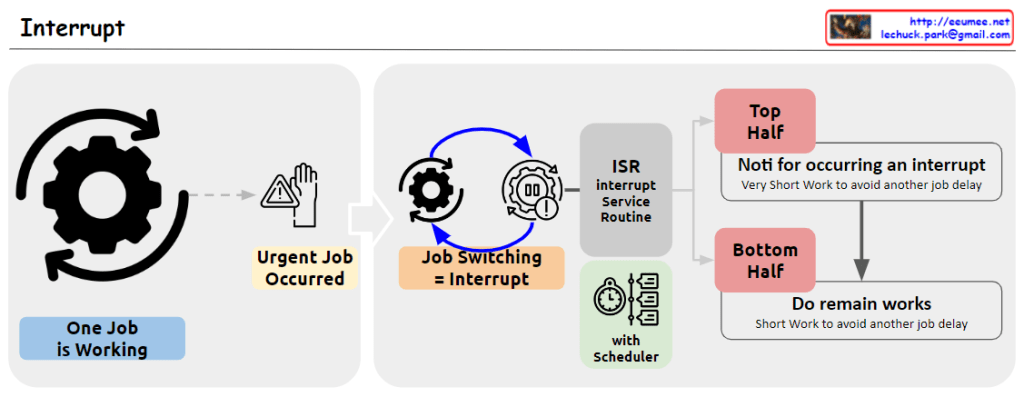
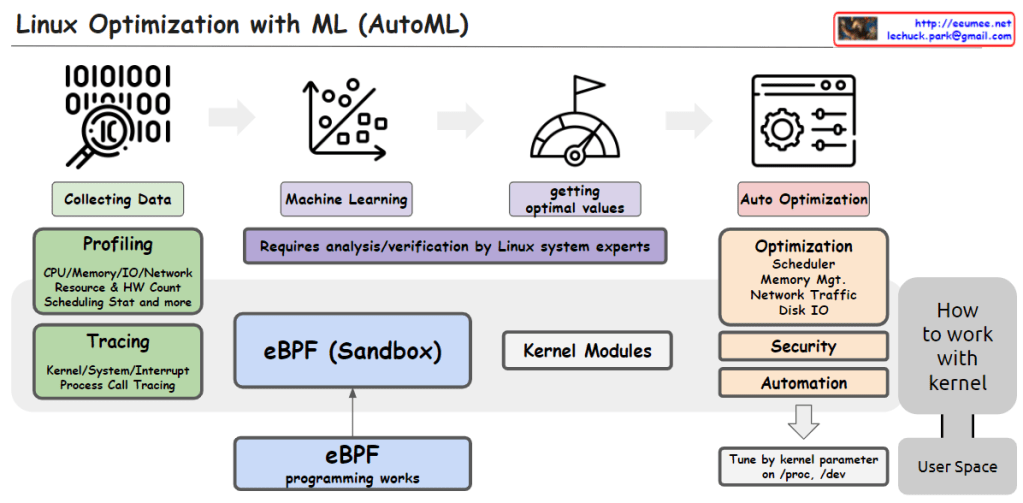
From Claude with some prompting
The image comprehensively illustrates the structure and major developments of the UNIX operating system, first developed in 1969. The key components and features are as follows:
- Hardware: The foundation of the system
- Kernel: The core of the operating system, including process management functions
- Shell: The interface for users to manage the system
- Utilities: Tools such as compilers included
- Daemon: Processes that run in the background
- C Language and Assembly: Introduced in 1972, the C language was used for system development
- POSIX (1988): An interface for standardizing UNIX systems, including pipes and filters
- Multitasking and Time-sharing: Key features of UNIX
- “All is File” Philosophy: A core design principle of UNIX
- Networking Advancements:
- UUCP (1978): An early communication protocol between UNIX systems
- TCP/IP with Socket API (1983): The foundation of modern networking
This diagram shows the evolution of UNIX from its basic structure to significant technological advancements over time, providing a comprehensive overview of UNIX’s core concepts and features. It displays the historical development of UNIX by combining early design elements with later added functionalities, allowing for a clear understanding of UNIX’s progression.