
Sunday morning, she wake up me
The Computing for the Fair Human Life.

Sunday morning, she wake up me


From Claude with some prompting
Let me explain this network diagram which illustrates packet processing and various network devices:
The diagram effectively highlights the complexity and redundancy in modern network architecture while suggesting a potential path toward more efficient packet processing through centralization.
This visualization emphasizes how current network infrastructure might benefit from consolidation of packet processing functions to reduce duplicated efforts and potentially lower costs.

From Claude with some prompting
This diagram effectively illustrates the core principles of machine learning.
Basic Components:
Key Messages:
This diagram showcases machine learning’s most powerful characteristic:
It’s similar to how physical laws like E = mc² can explain infinite natural phenomena with a single equation. The diagram effectively shows how machine learning serves as a powerful tool for discovering these fundamental patterns hidden within data.
The beauty of this concept lies in its simplicity and power:
This demonstrates the essence of machine learning: the ability to take finite observations and transform them into a universal rule that can make predictions far beyond the original training data.
From Claude with some prompting
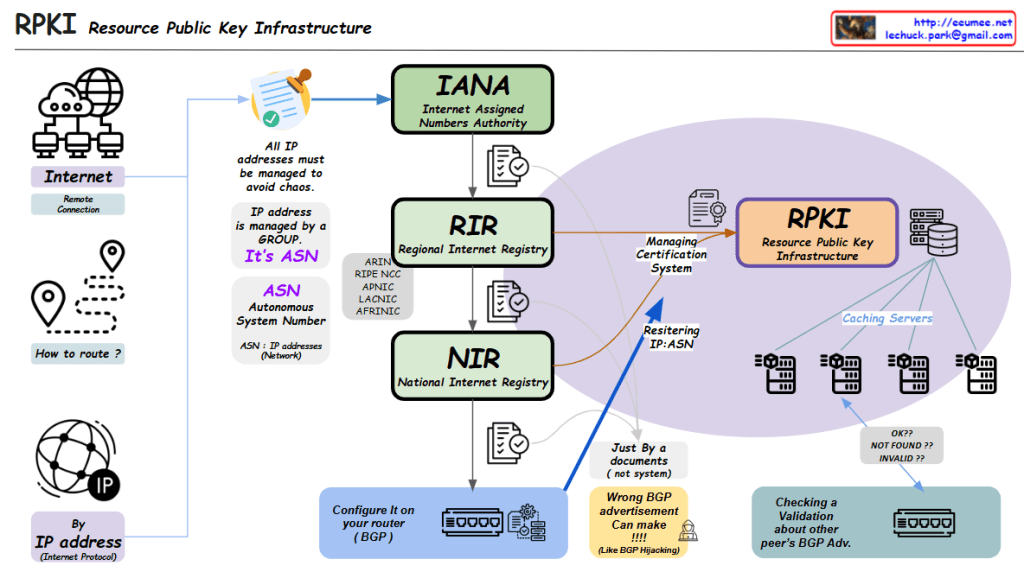
RPKI (Resource Public Key Infrastructure) Overview
1.1. Internet requires reliable IP management
1.2. Traditional IP address and routing system vulnerabilities
1.3. Need for secure and verifiable routing infrastructure
2.1. IANA (Internet Assigned Numbers Authority)
2.2. RIR (Regional Internet Registry)
2.3. NIR (National Internet Registry)
3.1. Resource Management
3.2. Technical Implementation
4.1. BGP Route Protection
4.2. Validation States
5.1. Enhanced routing security
5.2. Prevents unauthorized IP address use
5.3. Provides verifiable trust chain
5.4. Maintains internet routing stability
This RPKI-centric structure transforms traditional IP management into a robust, secure, and verifiable system for global internet routing infrastructure.
The system essentially creates a chain of trust from IANA through RIRs and NIRs down to individual network operators, ensuring the legitimacy of IP address usage and routing announcements.

From Claude with some prompting
This image depicts the structure of a system for controlling the operation of a motor. The key elements are:
This system represents an automated control system that continuously monitors the motor’s performance and maintains optimal operating conditions. It adjusts the motor settings based on sensor data, and uses feedback to optimize the performance.

From Claude with some prompting
This diagram illustrates different types of synchronization methods. It presents 4 main types:
The diagram progressively shows how each synchronization method operates, from simple unidirectional copying to more complex bidirectional process synchronization. Each method is designed to maintain consistency of data or processes, but with different levels of complexity and functionality. The visual representation effectively demonstrates the flow and relationship between different components in each synchronization type.
The image effectively uses icons and arrows to show the direction and nature of data/process flow, making it easy to understand the different levels of synchronization complexity and their specific purposes in system design.