From Claude with some prompting
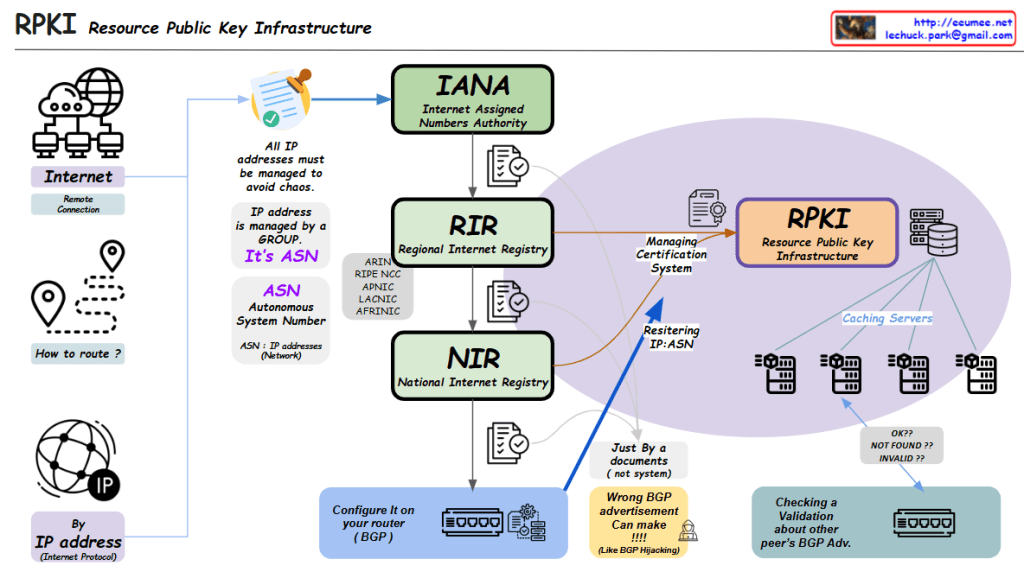
RPKI (Resource Public Key Infrastructure) Overview
- Background of RPKI Need
1.1. Internet requires reliable IP management
1.2. Traditional IP address and routing system vulnerabilities
1.3. Need for secure and verifiable routing infrastructure
- Core Components of RPKI Structure
2.1. IANA (Internet Assigned Numbers Authority)
- Top-level authority for IP resource management
- Oversees global IP address allocation
- Delegates authority to regional registries
2.2. RIR (Regional Internet Registry)
- Manages continental-level resources
- Key organizations: ARIN, RIPE NCC, APNIC, LACNIC, AFRINIC
- Handles certification management
2.3. NIR (National Internet Registry)
- National-level IP resource management
- Works under RIR guidance
- Manages local resource allocation
- RPKI Operational Process
3.1. Resource Management
- IP addresses grouped by ASN (Autonomous System Number)
- Systematic management to prevent chaos
- Certificate-based validation system
3.2. Technical Implementation
- Caching servers for RPKI data
- Router configuration using BGP
- Real-time validation of routing information
- Security Features
4.1. BGP Route Protection
- Prevents BGP hijacking attempts
- Validates peer BGP advertisements
- Ensures routing path integrity
4.2. Validation States
- OK: Valid route
- NOT FOUND: No RPKI record
- INVALID: Failed validation
- Benefits of RPKI
5.1. Enhanced routing security
5.2. Prevents unauthorized IP address use
5.3. Provides verifiable trust chain
5.4. Maintains internet routing stability
Summary
This RPKI-centric structure transforms traditional IP management into a robust, secure, and verifiable system for global internet routing infrastructure.
The system essentially creates a chain of trust from IANA through RIRs and NIRs down to individual network operators, ensuring the legitimacy of IP address usage and routing announcements.