From Gemini with some prompting
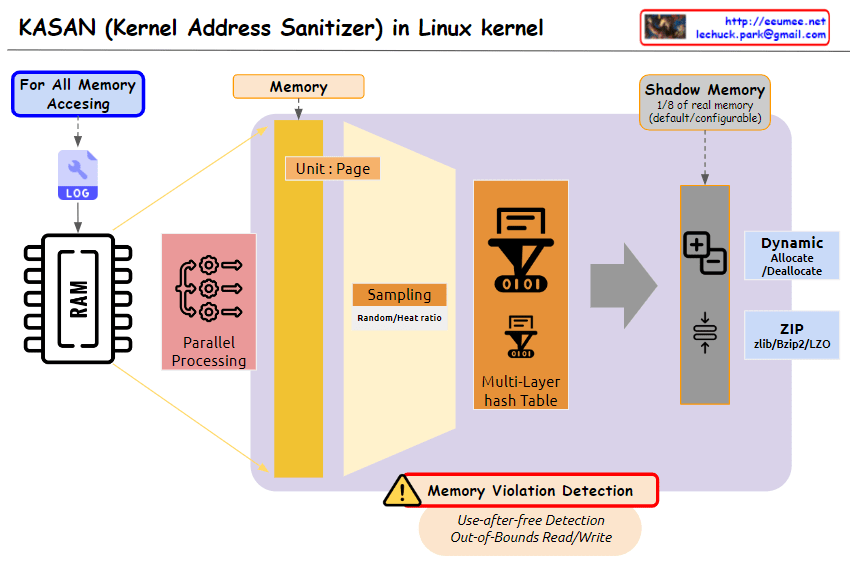
The image you provided depicts a diagram illustrating the operation of Kernel Address Sanitizer (KASAN) in the Linux kernel. KASAN is a memory sanitizer tool that aims to detect memory corruption errors, particularly those related to out-of-bounds reads/writes and use-after-free vulnerabilities.
Key Elements of the Diagram:
- Memory Accessing: This section represents the various ways in which memory is accessed within the kernel. It includes both valid and invalid access patterns.
- For All Memory: This indicates that KASAN monitors memory accesses for all allocated memory regions, regardless of their purpose or usage.
- Shadow Memory: This represents a dedicated memory space, typically 1/8th of the total physical memory, allocated by KASAN to store information about memory accesses.
- Violation Detection: This section highlights the core function of KASAN, which is to detect and report invalid memory access attempts.
- Use-after-free Detection: This specifically refers to KASAN’s ability to identify attempts to access memory regions that have already been freed, preventing potential memory corruption issues.
- Out-of-Bounds Read/Write: This emphasizes KASAN’s capability to detect memory accesses that exceed the boundaries of the allocated memory regions, safeguarding against buffer overflows and other memory-related vulnerabilities.
Overall Interpretation:
The diagram effectively illustrates the fundamental concept of KASAN: monitoring memory accesses, maintaining a shadow memory space for access information, and detecting invalid access patterns to prevent memory corruption errors.