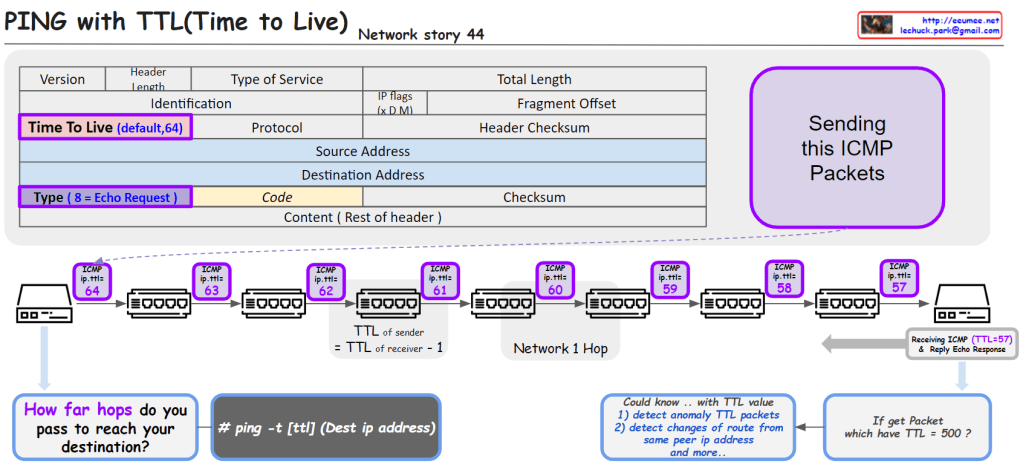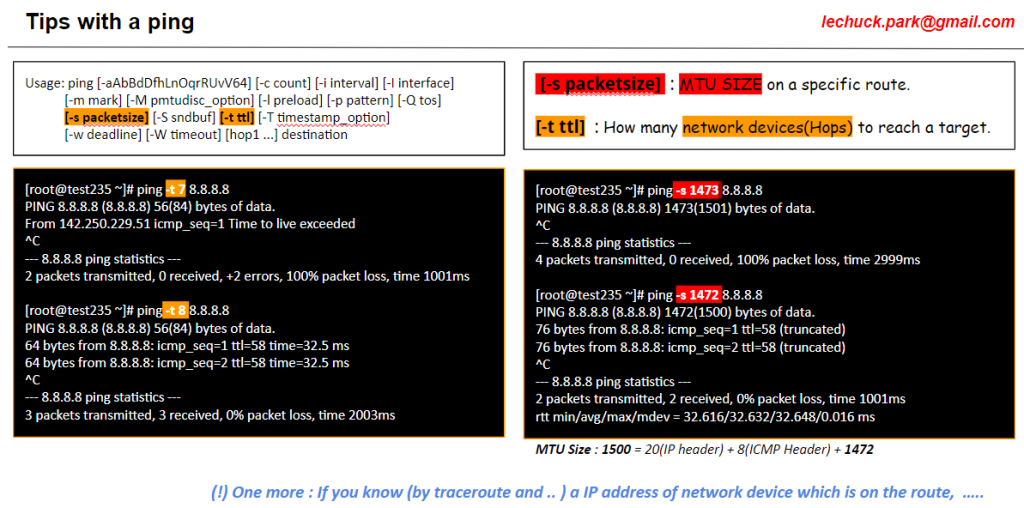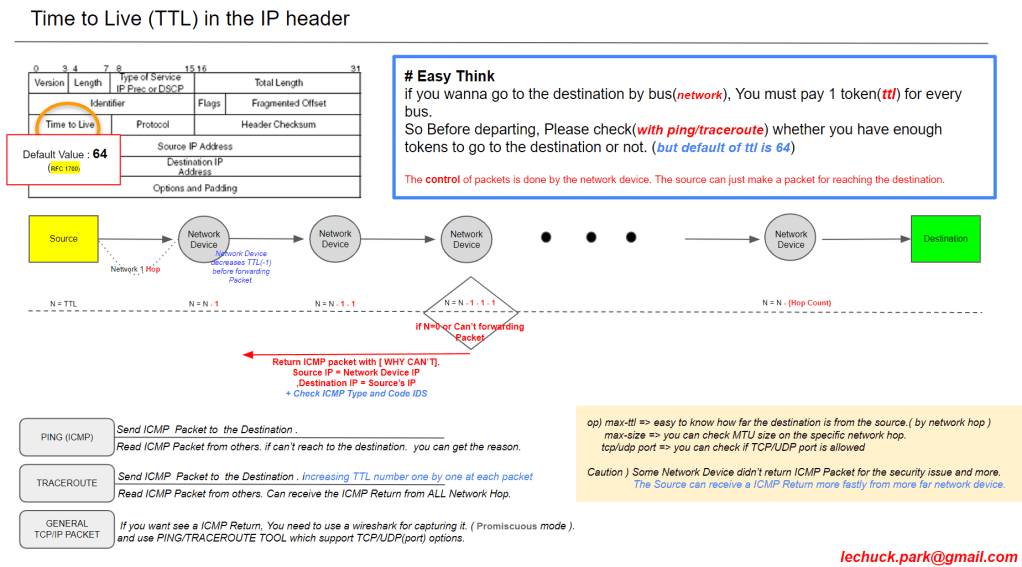
From DALL-E with some prompting
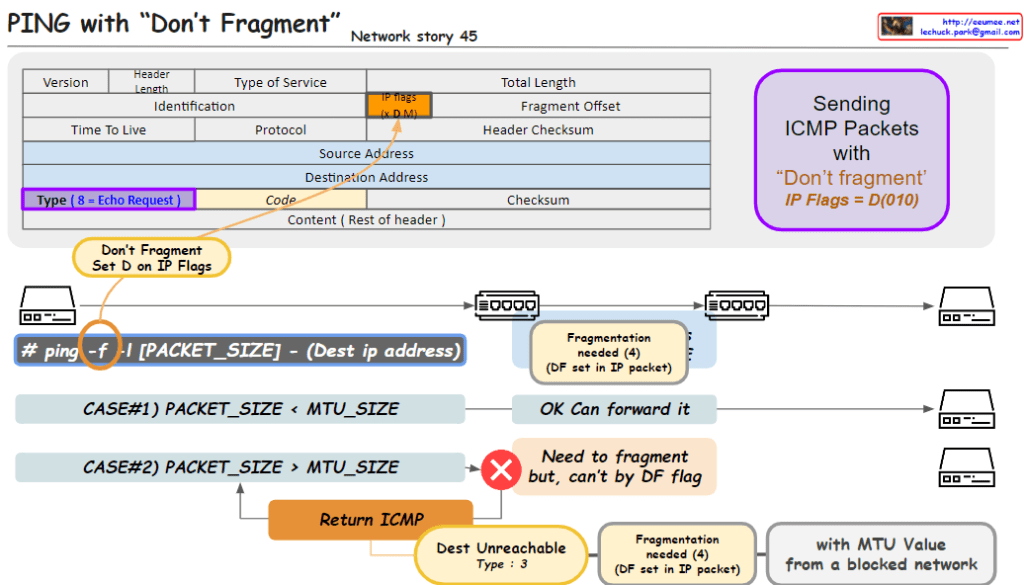
The image outlines a networking concept involving the transmission of ICMP (Internet Control Message Protocol) packets with the “Don’t Fragment” flag set, which is part of the IP (Internet Protocol) flags. Here’s a breakdown of the key elements in the image:
- Header Section:
- Type of Service: Indicates the quality of service for the packet.
- IP Flags: Contains the “Don’t Fragment” (DF) flag, indicated by setting the D bit to 0. The “MF” bit represents whether the packet is the last fragment.
- Type: For an ICMP Echo Request, this value is set to 8.
- Code: Used to further specify the message.
- Packet Transmission:
- The command
ping -fis used to send a ping with the DF flag set, which means the packets should not be fragmented, even if their size exceeds the MTU (Maximum Transmission Unit) of the network path. - Case #1: If the packet size is less than the MTU, the packet is forwarded without issue.
- Case #2: If the packet size is greater than the MTU, it needs to be fragmented. However, because the DF flag is set, it can’t be fragmented, resulting in a “Destination Unreachable” message with code 3 (Fragmentation needed and DF set).
- The command
- Error Handling:
- The ICMP error message “Destination Unreachable” with a code of “3” is returned if a packet with the DF flag set needs to be fragmented to continue along the network path but cannot be due to the flag.
This image is a guide to understanding how the “Don’t Fragment” flag in IP packets affects their transmission over networks and how ICMP is used for error reporting when the flag is set.