From DALL-E with some prompting
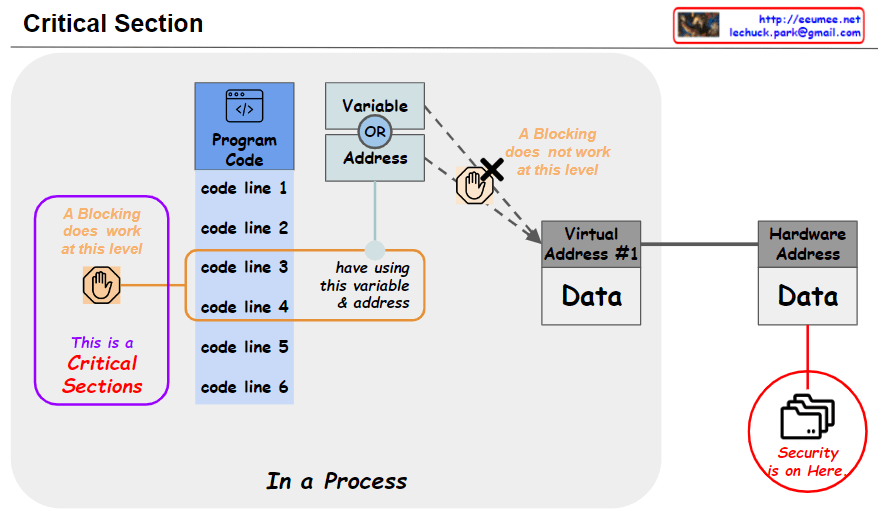
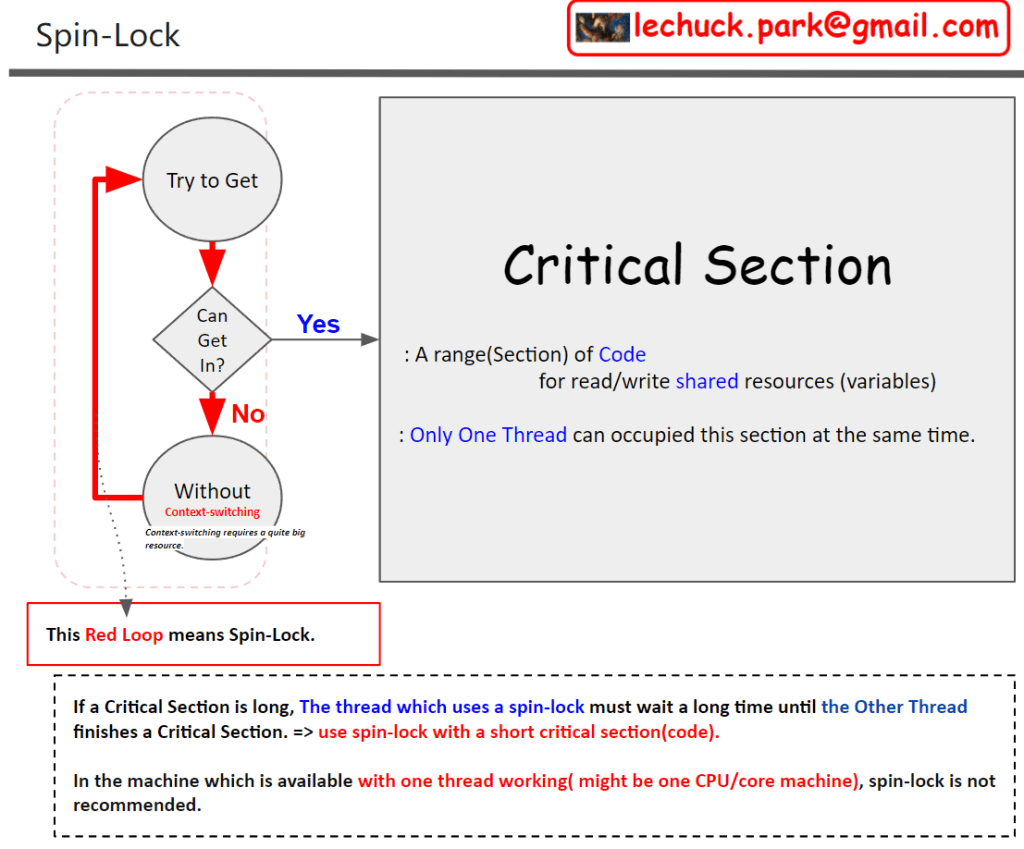
this image illustrates the concept of ‘Mutex (Mutual exclusion)’ and ‘Critical Section’ which are pivotal in multi-threaded programming. Mutexes are used to control simultaneous data access by multiple threads, maintaining data consistency. A critical section is a part of the code that only one thread can access at a time, and it’s where sensitive data is processed. Threads gain access to this section by acquiring a mutex lock (pthread_mutex_lock), and after completing their work, they release the lock (pthread_mutex_unlock) to allow other threads to enter. This mechanism ensures that all threads view and maintain a consistent state of the data, allowing safe modifications and sustained data integrity.